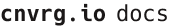# Anomaly Detection Blueprint - deprecated from 11/2024
# Inference
Anomaly detection involves distinguishing data variations, deviations, and exceptions from normal expectations for the purpose of detecting outliers in a dataset. Real-world examples of its use cases include detecting fraudulent transactions, adversary attacks, network intrusions, anomalous customers, and abnormal equipment behaviors.
# Purpose
Use this inference blueprint to immediately detect data anomalies or outliers in a dataset. To use this pretrained anomaly-detector model, create a ready-to-use API-endpoint that can be quickly integrated with your data and application.
This inference blueprint’s model was trained using anomalous customers based on their attributes and subscriptions to services. To use custom data according to your specific business, run this counterpart’s training blueprint, which trains the model and establishes an endpoint based on the newly trained model.
# Instructions
NOTE
The minimum resource recommendations to run this blueprint are 3.5 CPU and 8 GB RAM.
Complete the following steps to deploy an anomaly-detector API endpoint:
Click the Use Blueprint button.
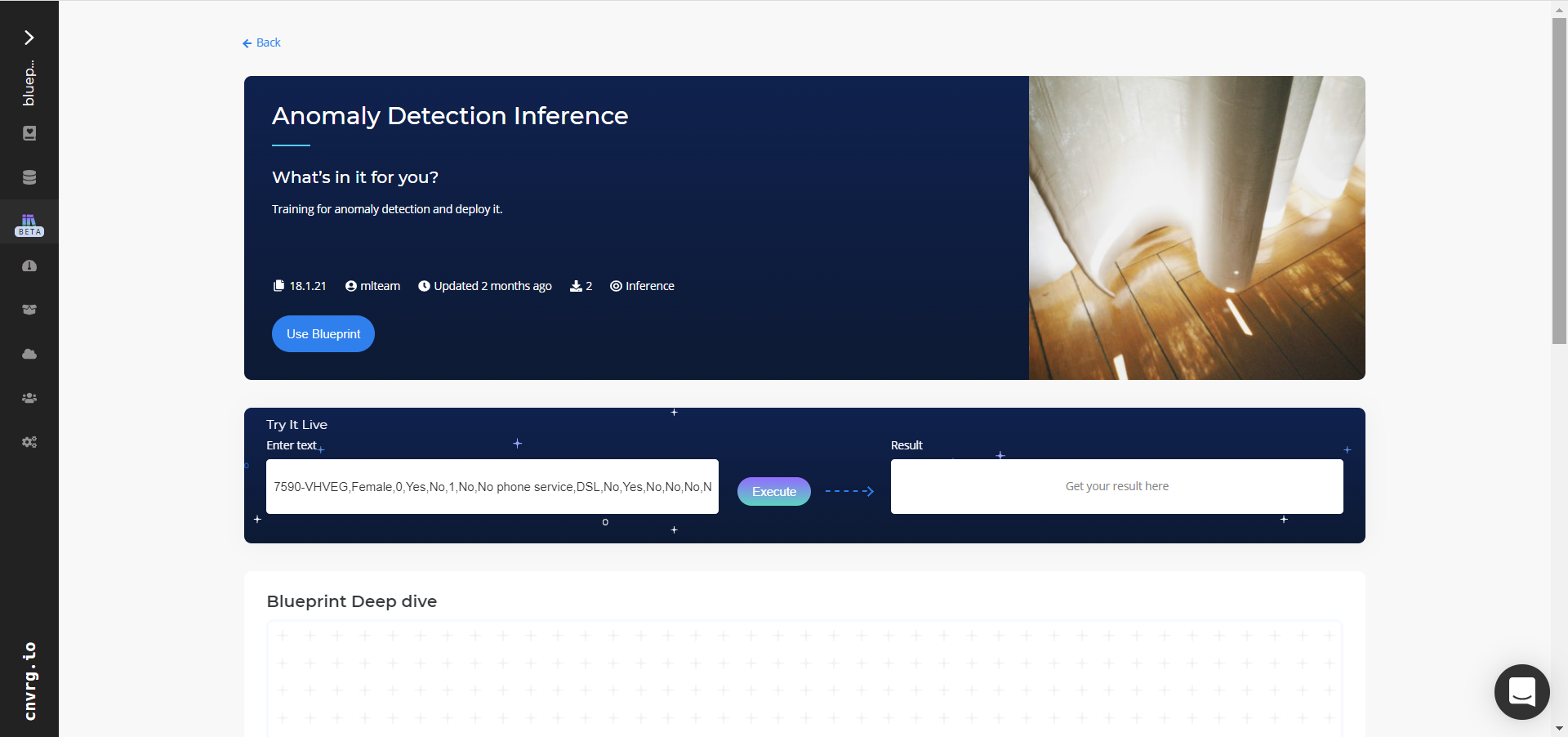
In the dialog, select the relevant compute to deploy the API endpoint and click the Start button.
The cnvrg software redirects to your endpoint. Complete one or both of the following options:
- Use the Try it Live section with any input data point to check your model.
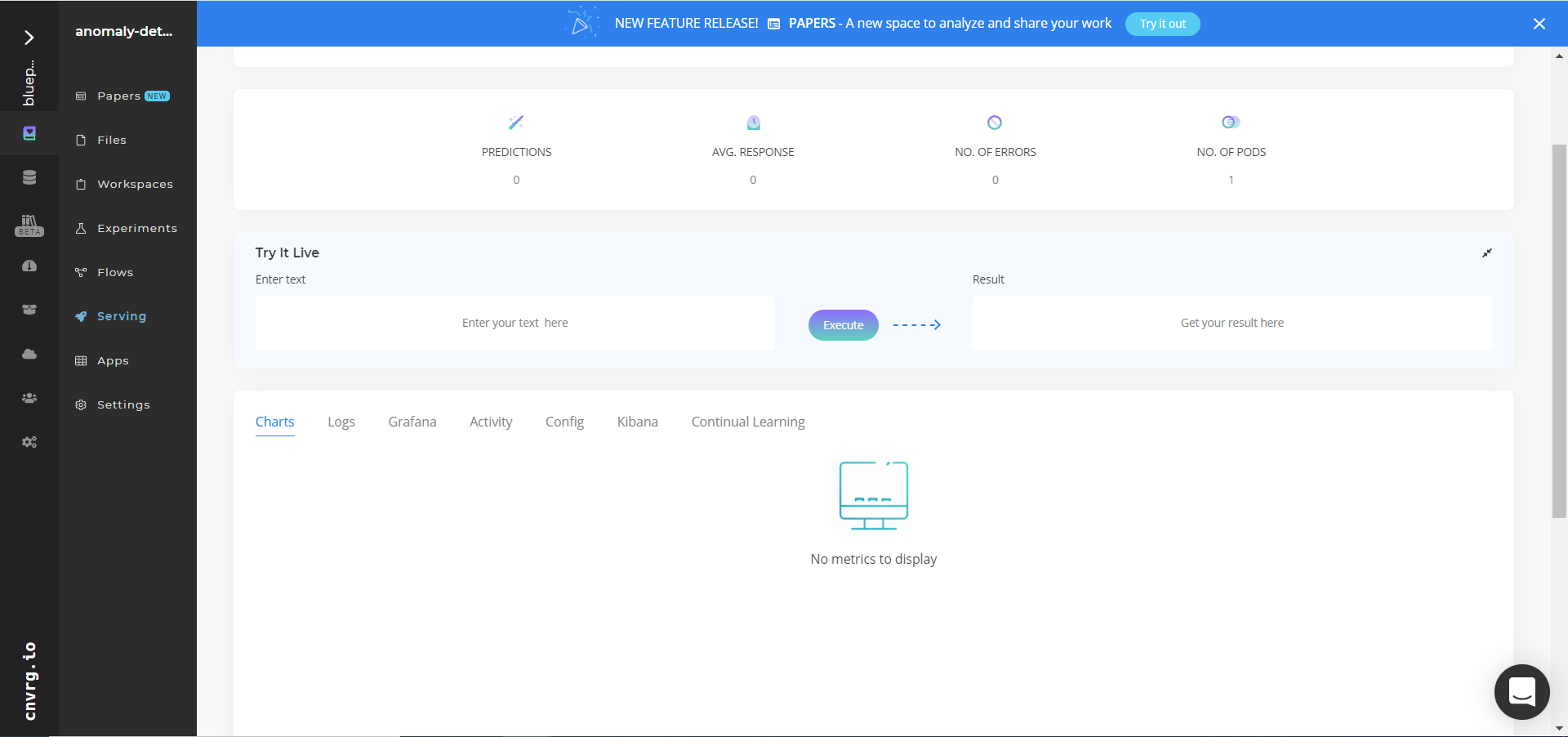
- Use the bottom integration panel to integrate your API with your code by copying in the code snippet.
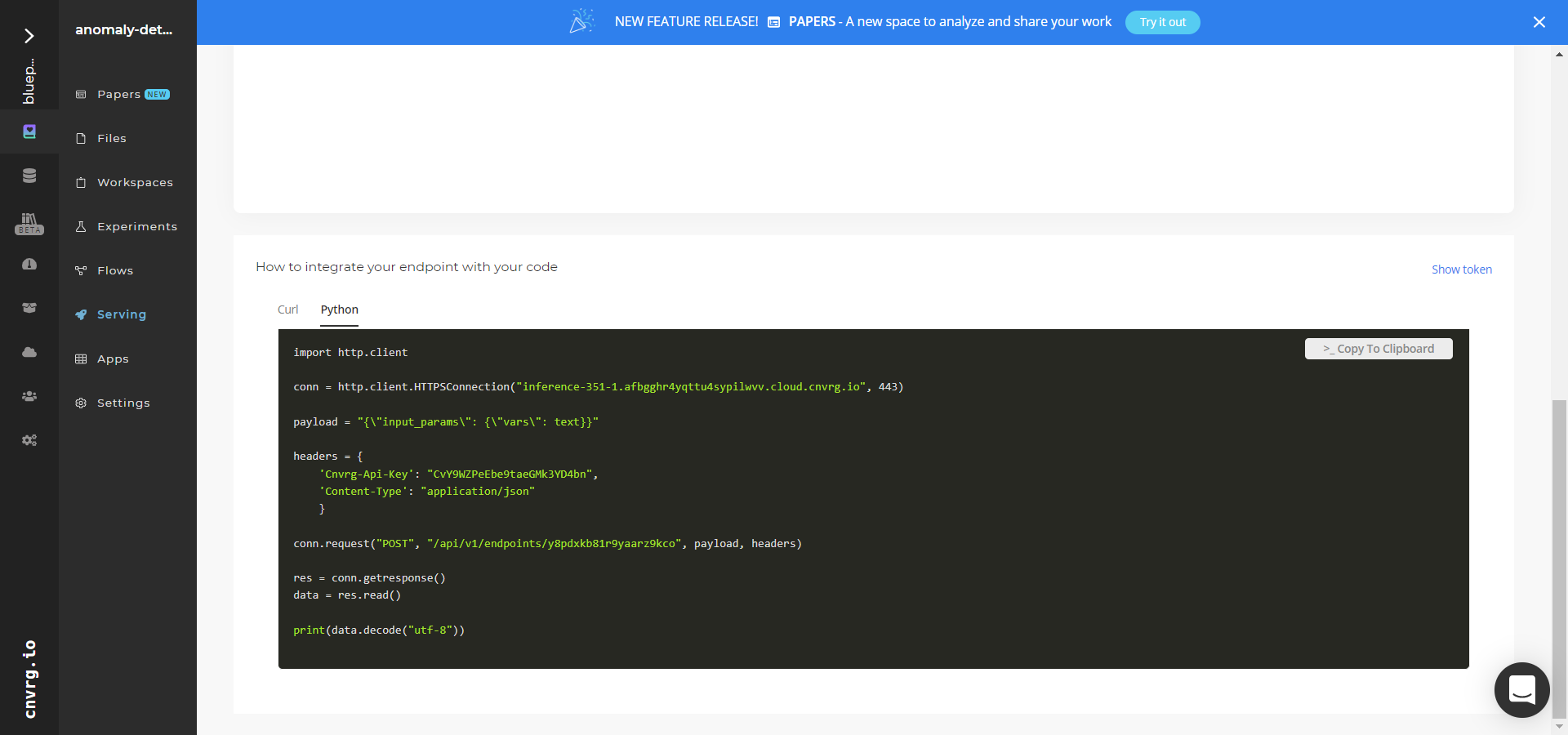
- Use the Try it Live section with any input data point to check your model.
An API endpoint that detects whether an input data point is an anomaly has now been deployed. For information on this blueprint's software version and release details, click here.
# Related Blueprints
Refer to the following blueprints related to this inference blueprint:
- Anomaly Detection Train
- InfluxDB ADTS Training
- S3 ADTS Training
- ADTS Inference
- Anomaly Detection Time-Series (ADTS) Train
- Anomaly Detection Time-Series (ADTS) Inference
# Training
Anomaly detection involves distinguishing data variations, deviations, and exceptions from normal expectations for the purpose of detecting outliers in a dataset. Real-world examples of its use cases include detecting fraudulent transactions, adversary attacks, network intrusions, anomalous customers, and abnormal equipment behaviors.
# Overview
The following diagram provides an overview of this blueprint’s inputs and outputs.
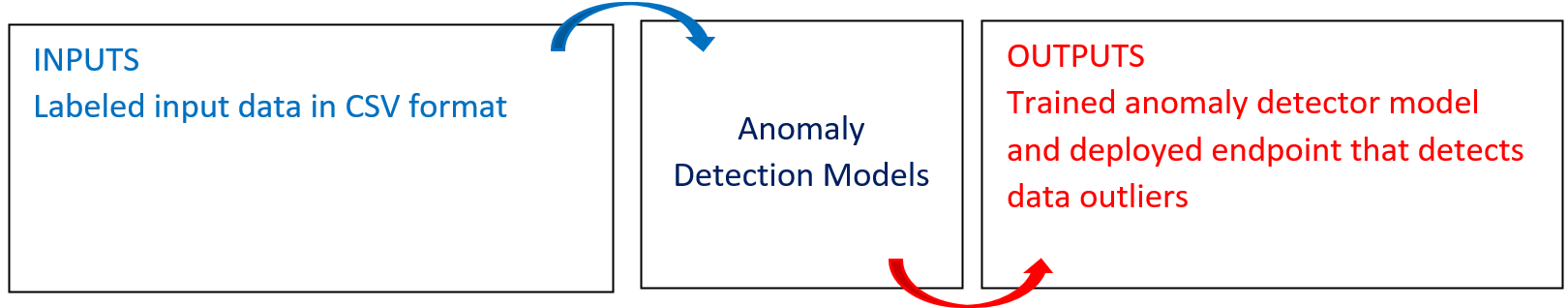
# Purpose
Use this training blueprint to train multiple algorithms and identify the best performer to detect data anomalies or outliers. This blueprint also establishes an endpoint that can be used to make inferences for anomaly detections based on the newly trained model.
This is a one-click, train-and-deploy blueprint for predicting data anomalies. Place the labeled input data in CSV format in a connector such as S3 or Splunk, which the blueprint uses to train multiple algorithms. The best performing algorithms are selected and deployed as an API endpoint. Then, users can call this API on new data points and view responses whether the new data points are outliers.
# Deep Dive
The following flow diagram illustrates this blueprint’s pipeline:
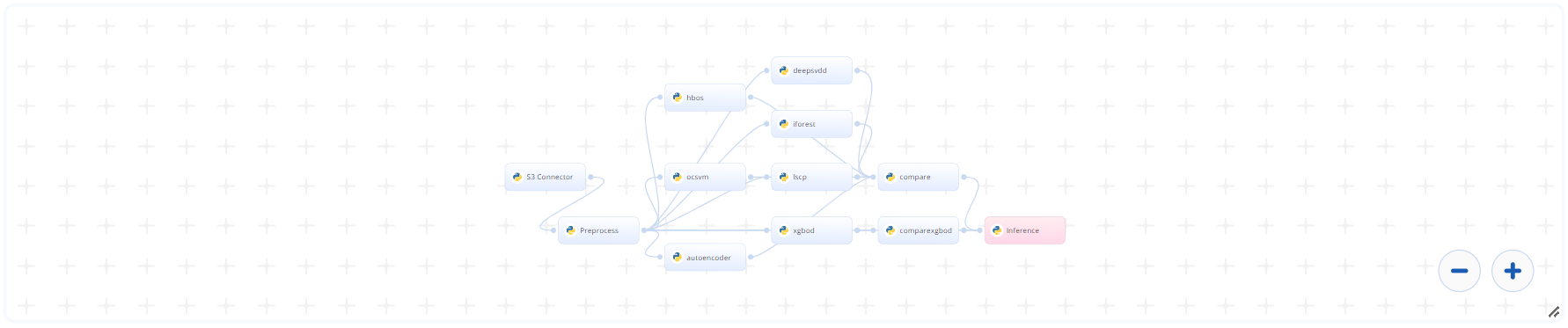
# Instructions
NOTE
The minimum resource recommendations to run this blueprint are 3.5 CPU and 8 GB RAM.
Complete the following steps to train an anomaly-detector model:
Click the Use Blueprint button.
In the dialog, select the relevant compute to deploy the API endpoint and click the Start button.
The cnvrg software redirects to your endpoint. Complete one or both of the following options:
- Use the Try it Live section with any input data point to check your model.

- Use the bottom integration panel to integrate your API with your code by copying in the code snippet.

- Use the Try it Live section with any input data point to check your model.
An API endpoint that detects whether an input data point is an anomaly has now been deployed. For information on this blueprint's software version and release details, click here.
# Connected Libraries
Refer to the following libraries connected to this blueprint:
- S3 Connector
- Anomaly Detection Preprocessing
- Anomaly Detection AutoEncoder
- Anomaly Detection Deep SVDD
- Anomaly Detection LSCP
- Anomaly Detection iForest
- Anomaly Detection OCSVM
- Anomaly Detection HBOS
- Anomaly Detection XGBOD
- Anomaly Detection Comparexgbod
- Anomaly Detection Compare
- Anomaly Detection Inference
# Related Blueprints
Refer to the following blueprints related to this training blueprint: